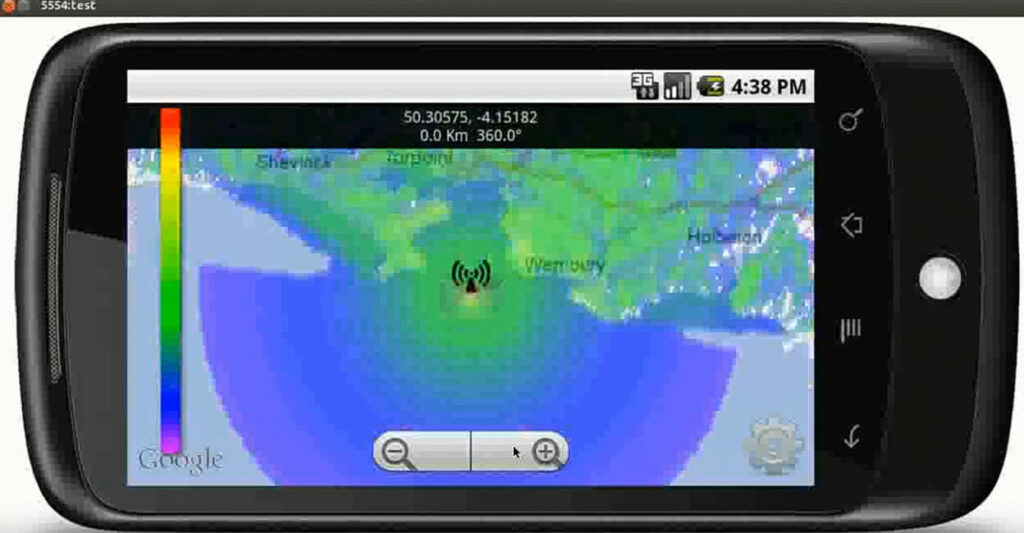
Team Awareness Kit (TAK) has become the poster-child for defence innovation, transforming mapping, command and control and situational awareness with a relatively lightweight smartphone app. Never in the history of defence procurement have so many forces, nations and equipment vendors achieved tactical interoperability with impressive results.
Key to it’s success is a permissive software license, APIs and a design focused on information standards.
2023 Q2 update: We have a ATAK plugin:
Read this waffle if you want but if you just want a capability on ATAK, get the plugin here:
https://cloudrf.com/atak-plugin
Background: Too many maps
Historically defence procurement has failed to differentiate between standards (eg. KML) and software (eg. Google Earth) resulting in many duplicate apps, especially multi-source maps solving the shortcomings of the previous multi-source map, which is the military implementation of the famous too-many-standards XKCD sketch. The revolving door of senior officers into defence companies didn’t help the situation. This reached a fever pitch during operations in Afghanistan 2006-2014 where at one point, every service, nation and prime contractor were plugging their own “multi-source” map, all of which were trying to solve the same problem, and all of which compounded it. Analysts were motivated to write glue-ware to achieve interoperability, typically with visual basic due to the locked down environment.
In our experience, the enduring military map was none of the above, it was good old Google Earth which could be found at all command levels due to its simplicity and assured interoperability via KML and HTML standards.
ATAK has disrupted a long established pattern of short sighted procurement of incompatible point solutions – which was long overdue and best of all, the IPR is not owned and controlled by a single contractor.
The TAK plugin industry
TAK is produced and owned by the US Government. Despite most of the client source code being available on the Play store and elsewhere a documented SDK for plugin developers, plugins require US Government approval. This approval is more than a bureaucratic hurdle, it is a security, technical and cryptographic approval which requires a code-review and a code signing certificate. There are a limited number of public domain signed plugins and a greater number of private plugins.
Given the cultural change of not just using open source in defence, but publishing and maintaining it, on public app stores it was inevitable there would be a catch to appease committees.
To get US Government approval requires a sponsor aka a contract. There are many firms large and small developing TAK plugins (typically with Java or Kotlin) under contract, including foreign nations under trade agreements. Whilst Android app development might sound a little 2010 (CloudRF started as a Android app in 2011) it’s made lucrative by the exclusivity of needing a Government sponsor – to publish at least.
2010 called, they want Java back..
Java has had its day in our opinion. It created a generation of software developers who exist in a (JVM) bubble of abstraction far away from the processor for whom an opcode is an alien concept and writing a Hello world! demo on a vanilla machine requires a disproportionate amount of IDE massaging and preparation. The effort used to be justifiable because of the security the Java sandbox brings. The recent log4j CVE undid that argument pretty well.
We used Java 10 years ago to make our debut app “RFSignal” during the app gold rush of 2011 along with the Android SDK. It worked well for the first few releases whilst the app was under active development but the cracks showed when the app transitioned to maintenance. We found the “Eclipse” dev environment itself to be a substantial burden and even small one-line changes required an inordinate amount of effort in many places compared with other languages like Python, PHP or C++. Back then Android was evolving rapidly and keeping up with the latest SDK was a task in itself so we were glad to retire the app in 2015 and move to a SaaS model (and not give Google 30% of our sales).
We vowed no more Java, and to date have kept our promise except we did reference 1 line from the old app relating to a PNG hack to achieve Android bitmap opacity which was funny – ten years later.
To be clear we’re not criticising ATAK plugins written in Java – there is a clear need or them, especially interfaces to hardware which is a great value-add for manufacturers. We are proposing a more agile plugin architecture based around standard and network APIs which doesn’t prescribe a programming language – or even an OS.
ATAK source code: https://github.com/deptofdefense/AndroidTacticalAssaultKit-CIV
Standards to the rescue
We came late to ATAK in late 2020 but were no strangers to information standards, reverse engineering and joining distinct systems, at no extra cost, which our founder had previously won a national award for in 2012.
We already had a Google Earth layer (written in PHP) which relied heavily on the KML standard to connect CloudRF to Google Earth. We attempted the same on ATAK 4.1 without success due to limited KML GroundOverlay support back then. We could load on some layer types with a 10 second minimum refresh but advanced network features such as KML’s view based Link were not implemented. We use this feature to fetch the viewer’s bounding box, and center point, in our Google Earth KML interface.
During our research we learnt about the Cursor-on-Target (CoT) XML schema and how it was implemented within ATAK’s Geochat functionality. This allowed us to close the loop and handle a chat message from a client at our own TAK server – without touching Java!! Being able to connect the client to our own server was significant, and exciting, as this is where we could house, and maintain, our code instead of a version-brittle plugin.
An open source TAK server….with a Python bot
Realising we needed a TAK server capable of talking CoT we headed to Github and found two open source projects, FreeTakServer and Taky, both written in Python. We tried both and selected the simpler Taky server which offered a minimal setup necessary for 2 way communication.
You can find an early ATAK capability we published for OSGB coordinates conversion bot over here.
One of the nice features about SaaS models is licensing. You can connect software modules via a common protocol with different licenses. This is why we open sourced our server modifications but kept our Python bot private. You can get a head-start for how to build a bot with our open source geobot.
We extended taky and added some features relating to client authentication, access control, anonymity and CoT. The CoT modification is notable as it extends the namespace (which is permitted in the XML standard) to tag anonymous messages with the originator’s unique ID. These modified messages are exchanged between the chatbot and the server when sharing shapes and are redundant for regular C2 use.
UPDATE: We no longer use Taky since OG TAK server was published!
‘Follow-me’ demo
This early demo was created with a GPS spoofer (visible in corner). When the position updates, ATAK sends a broadcast which our TAKY server receives. The python bot at the server forwards this to the API and a creates a KML layer – a standard feature in CloudRF. On ATAK, a network KML layer pulls back the KML on a periodic cycle which is why it is slow to catch up when the marker moves fast. We have since identified a mechanism to return a KMZ immediately using a data package.
SSL, HTTPS and Data packages
Achieving insecure communication was quick: We published a demo of a CoT + KML script which did this in Nov 2020. Achieving secure communication with TLS certificates, which worked on ATAK and for HTTPS was a different matter and required lots of debugging. A lot of time was spent resolving seemingly trivial issues but the key principle we found which unlocked a lot of happenings was adding the right SAN (SubjectAltName) to our web server certificates.
SAN is used as an optional field in SSL certificates to declare alternative names or IP addresses, and is checked by Android’s SSL client. The open source TAK servers would wrap a script called ROTC.py to generate certificates (without SAN) using a self-signed certificate authority (CA) which despite the manageable security risk involved works well for securing the ATAK server – and even mutual authentication which we have implemented.
When ATAK later makes a request to a HTTPS link to fetch a data package for example, it checks the certificate for a SAN which a third party certificate from a trusted CA typically has. This tiny little attribute is worth big money as they can add lots in an array and call it a “wildcard” certificate. Thankfully LetsEncrypt is disrupting this monopoly.
Data packages are zip archives used in TAK to share files. They require a manifest file and a simple folder structure. When a CoT message is delivered to a End User Device (EUD) describing a data package it will fetch it, unpack it and auto-parse the content. We return KMZ files but you can also return XML map files to add map sources for example.
Self hosted solution?
We have a turnkey server with the CloudRF API, OSM tile server and ATAK interface called SOOTHSAYER. It’s ideal for rescue organisations and first responders who might otherwise be running multiple network services or working areas without internet access.
UPDATE: WE NOW HAVE A PLUGIN
After all this, we went and made a plugin anyway: